Emerging Technologies
According to technology researchers, there will be 220 million connected cars all around the world and about 5.8 billion IoT endpoints in 2020. With such advancements, the terror of attacks in cyberspace is on a rise.
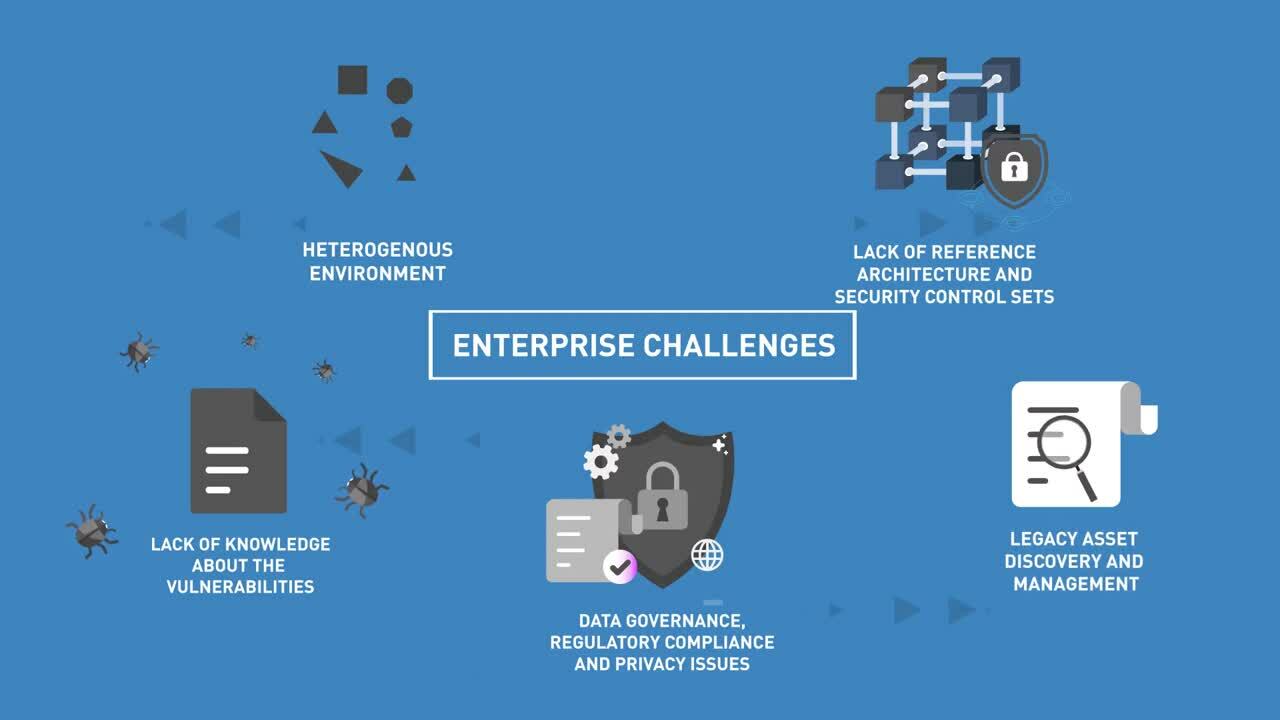
Insights
Get a deeper understanding of our Emerging Technologies service offering
How we can help
Building new age solutions with our Emerging Technologies services
OT Security
We help organizations define OT security reference architecture and security engineering through our ‘Secure by Design’ and ‘Secure by Scale’ approach. Our IoT security framework helps in enhancing security posture of OT infrastructure, OT devices, OT platforms, and IT/OT convergence.
Data Governance and Regulatory Compliance for OT Industry
We assess and build secure data governance in OT environment by analyzing the gaps based on regulatory compliance standards. We help to implement the security controls and monitor them continuously to meet regulatory compliance guidelines.
Security Frameworks for Connected Devices, Blockchain and API Platforms
We secure emerging technologies via our approach of ‘Secure by Design’ , ‘Secure by Scale’ , and ‘Secure the Future’ . We have developed security frameworks for connected devices, blockchain, and API platforms. We also offer design, implementation, and assessment services to secure these technology initiatives.
Success Stories
Implementing and monitoring security platforms across client’s OT, IoT, and blockchain environment
Our Offerings
We help our clients embed security controls into the design, implementation, and risk assessment phase with emerging technologies like IoT, OT, blockchain, and RPA
Other Solutions
Secure Design
Design of security principles, review of design, and architecture of IoT/OT infrastructure.
Secure Cloud
Security release and deployment of IoT devices on cloud. This includes security assessment and review of the underlying cloud infrastructure, applications, and platforms connected to the devices and ensures that adequate security controls are enabled on the cloud.
Secure Platforms for IoT/OT
Security engineering, secure code review, and assessment of IoT/OT platforms. Enabling secure integrations of applications with connected devices. Monitoring and managing the inventory for the connected devices.
Device Security
IoT/OT device security consists of security assessment and testing of firmware/devices, API/HW interfaces, standard cryptography implementation and key management, data security at rest, and in transit for any associated risks.
Communications
Ensuring secure communication channels at transport level, assessment of the communication protocols, its secure implementation, and data payloads security.
Compliance
Configure and manage OT assets in adherence to enterprise security policies and changing regulations. Compliance assessment and readiness for IEC/ISA 62443, NIST 800-82, ISO 27001.
Managed Services
SOC integration of IoT/OT logs, events, and monitoring of IoT/OT assets through SOC networks.
Secure Applications
Perform code review of blockchain applications and assessments of the third-party applications integrated with the blockchain platforms.
Secure Platforms for Blockchain
Black-box and grey-box security assessments for private blockchain platforms, ledgers, nodes, dockers, and the underlying infrastructure. Management of crypto keys across all participant nodes and ensuring secure crypto implementation in blockchain ecosystem.
RPA - Advisory and Assurance
Design and review bot security architecture, standardize processes, and vulnerability assessment program.